5 Essential Steps to Ensure Reliable and Thorough Background Checks for Gig Workers

Gig and on-demand workforces create unique screening challenges: variable volumes, diverse role risks, and rules that change by location. This guide lays out a five-step framework to deliver dependable, thorough background checks for gig workers while preserving speed, candidate experience, and legal compliance. You’ll learn how to classify role-specific risk, match screening components to those risks, apply FCRA and state-level requirements, use modern verification technology, and set up continuous monitoring so your workforce stays safe over time.
Each section includes practical checklists, decision matrices, and operational tactics HR teams can apply right away to reduce onboarding friction and limit exposure. Recommendations focus on role-based prioritization, measurable turnaround targets, and clear candidate communication so platforms can scale trust without sacrificing legal safeguards. We also cover AI-driven workflows and a specialist-provider approach, and we offer an option to book a Vetty demo if you want to see the platform in action.
How Do You Define Screening Needs Based on Gig Worker Role Risks?
Start by grouping gig roles by the type and level of risk they introduce, then map those groups to specific screening components. That creates repeatable, defensible decisions that avoid over-screening low-risk roles while ensuring high-risk workers receive necessary checks like driving records or enhanced identity verification.
Focus your assessment on a role’s contact with people, access to property, and handling of sensitive data to build a consistent rule set that speeds hiring and improves fairness at scale. The following sections break down core risk categories, recommend screening packages for common gig roles, and provide a concise role-risk matrix for quick operational use.
What Are the Key Risk Categories for Different Gig Worker Roles?
Risk categories make it clear which checks are essential and which are optional based on duties and exposure. Low-risk roles typically have limited direct contact or property access and usually require identity verification and a basic criminal search. Medium-risk roles—those with customer interaction or limited access to homes or vehicles—should include employment or credential verification plus a more detailed criminal history. High-risk roles—transporting people or goods, caregiving, or accessing sensitive data—often need driving-record checks, enhanced identity verification, and role-specific license or credential confirmation. Use a simple scorecard—Exposure (0–3) + Vulnerability (0–3) + Access to assets (0–3)—to prioritize which checks to run.
Which Background Check Components Are Recommended for Each Gig Role?
Map checks to role risk so screening templates balance speed and coverage and set realistic turnaround targets. Common components include criminal background searches, identity verification, driving-record checks for transport roles, employment or credential verification for professional services, and drug testing where it’s lawful and relevant. Optional add-ons—education checks or enhanced international searches—should be reserved for roles where those details materially affect safety or service quality. Turnaround times vary: identity and automated criminal searches often finish in 24–72 hours, while manual verifications or international checks may take longer—so run checks in parallel when speed matters.
| Gig Role | Primary Risk Type | Recommended Screening Components & Priority |
|---|---|---|
| Delivery driver | Vehicle operation, public safety | Driving record (high), criminal check (high), identity verification (high) |
| In-home caregiver | Vulnerable population exposure | Enhanced criminal check (high), identity verification (high), credential/license check (medium) |
| Platform consultant (remote) | Data access, reputational risk | Identity verification (high), criminal check (medium), employment/credential verification (medium) |
| Task-based laborer | Property access, tool safety | Criminal check (medium), identity verification (high), insurance/authorization review (optional) |
This matrix standardizes screening by role and defines the minimum acceptable package for activation. Use it as an operational template to reduce ad-hoc decisions and keep consistent safety standards across high-volume hiring.
Gig Economy Challenges: Monitoring, Analysis, and Risk Mitigation
The gig economy—built on temporary, freelance, and platform-mediated work—creates distinct monitoring and analysis challenges for employers (see Manyika et al., Independent work: choice, necessity, and the gig economy, McKinsey Global Institute, 2016). Its strengths—flexibility and scale—coexist with risks such as income instability, limited benefits, and evolving legal exposure (see Heeks, Decent work and the digital gig economy, University of Manchester, 2017). Employers use a range of tools to manage these challenges: time-tracking, performance analytics, GPS/location tools, task management, rating systems, blockchain reputation models, and integrated platform solutions. Each approach has trade-offs in accuracy, privacy, fairness, and complexity. Ongoing research and product design focus on improving oversight, quality control, and feedback mechanisms so platforms can capture the benefits of flexible work while limiting downside risks.
Gig Economy, Analysis and Monitoring: Prioritizing Privacy, Performance, and Accuracy, D. Mehta, 2024
What Are the Legal and Regulatory Compliance Requirements for Gig Worker Background Checks?
Compliance starts with identifying which laws apply and building a documented, repeatable process that meets notice, consent, and adverse-action requirements while respecting jurisdictional limits on criminal-history use. The Fair Credit Reporting Act (FCRA) governs many consumer-report-based checks and requires a standalone disclosure, written authorization, and specific pre-adverse and adverse-action steps when screening results affect hiring. Ban-the-Box and other local laws can limit when and how criminal-history questions are asked, so keep a living regulation matrix and enforce location-aware rules. International hires may trigger GDPR or similar privacy obligations, adding requirements for lawful basis, transparency, and data retention. The sections below summarize
FCRA applicability and state/Ban-the-Box considerations and include a compact compliance checklist and a regulatory mapping table for HR teams.
How Does FCRA Compliance Apply to Independent Contractors?
FCRA applies when a third-party consumer reporting agency provides background information used to make hiring or engagement decisions—which can include independent contractors and gig workers if the report affects selection, assignment, or retention. Practically, you must provide a standalone disclosure that a consumer report may be obtained, get written consent before ordering the report, and follow the pre-adverse action process—sharing the report copy and a summary of rights—before taking adverse steps. If an adverse action occurs, send the required final notice. Centralize disclosure templates, timestamp consent capture, and retain records to demonstrate compliance, especially in high-volume or automated
workflows.
What State-Specific and Ban-the-Box Laws Affect Gig Worker Screening?
State and local laws differ on timing, permissible questions, and how criminal records may be used—so a one-size-fits-all policy creates legal risk. Ban-the-Box rules often delay criminal-history inquiries or limit consideration of certain offenses; other jurisdictions cap how old records can be or require individualized assessments before disqualification. Operationalize compliance by maintaining a live jurisdictional table, routing candidate screens through location-aware rules, and training automated decision logic to apply fair-chance assessments where required. Embed state rules into screening templates and ensure audit logs record the rationale for each adverse action.
| Regulation | Applicability to Gig Workers | Required Steps / Practical HR Checklist |
|---|---|---|
| FCRA | Applies when consumer reports are used for hiring/engagement | Use standalone disclosure, obtain written consent, send pre-adverse and adverse action notices; retain records |
| Ban-the-Box / Local Fair-Chance Laws | Timing and scope restrictions vary by jurisdiction | Delay criminal-history inquiries where required, perform individualized assessments, document business necessity |
| State-specific criminal record rules | May limit use of old convictions or certain offense types | Maintain per-state rules, automate rule application, update matrices quarterly |
| GDPR / International privacy laws | Applies to EU hires or processing of EU personal data | Establish lawful basis, provide transparency notices, limit retention, enable data subject rights |
This table translates core regulations into practical HR actions to help you remain compliant while screening gig talent.
How Can Advanced Technology Improve Speed and Accuracy in Gig Worker Background Checks?
Modern technology—AI-driven matching, automation, and digital identity verification—removes manual bottlenecks and raises match accuracy by correlating fragmented records and verifying identities at scale. Automation handles routine steps like consent capture, parallel ordering of searches, and result normalization, cutting time-to-activation and improving consistency. AI helps link records, detect anomalies, and surface cases that need human review; governance and bias controls are essential to keep decisions fair and auditable. The sections below describe AI use cases and how
digital identity verification strengthens on-demand vetting, plus a brief example of a streamlined verification flow.
What Role Does AI Play in Automated Screening and Identity Verification?
AI speeds up screening by automating record linkage across databases, flagging inconsistent data, and prioritizing cases for human review. Machine learning can reduce false matches by accounting for name variations, address history, and contextual metadata to improve identity resolution. AI also enables automated redaction and categorization so reviewers see only legally relevant information. Best practices include human-in-the-loop review for adverse actions, bias testing on training data, and deterministic rules for legally sensitive criteria to preserve fairness and auditability.
How Does Digital Identity Verification Enhance On-Demand Workforce Vetting?
According to Gartner as seen in the HR Gazette, by 2028 some 25% of candidate profiles worldwide will be fake making digital identity verification a crucial part of the hiring process. Digital identity verification combines document validation, biometric checks, and database cross-references to confirm a candidate’s identity before deeper checks begin. A common flow collects a government ID, runs automated document authentication, performs a biometric selfie match, and cross-checks known identity sources to generate a confidence score. This reduces impersonation and fraud, improves the accuracy of downstream criminal and license checks, and speeds activation by resolving identity issues up front. Require stronger verification for high-risk roles and lighter verification for low-risk tasks to balance friction and security.
Note: When evaluating technology partners, prioritize platforms that blend automated identity verification with workflow orchestration and compliance controls. If you want to see an integrated solution that supports verification and onboarding, book a demo of the Vetty platform.
Why Is Continuous Monitoring Important for Ongoing Gig Worker Compliance and Safety?
Continuous monitoring means automatically checking for new records or status changes after a worker is cleared, shifting from one-time screening to ongoing oversight. This approach detects new incidents—arrests, license revocations, credential lapses—so platforms can act quickly to protect customers and stay compliant. Continuous monitoring reduces the need for repeated full re-screens, lowers manual workload, and protects brand reputation by catching issues that arise post-onboarding. The sections below outline the benefits and an
alert-triage workflow to make monitoring actionable instead of noisy.
What Are the Benefits of Continuous Background Monitoring for Gig Workers?
Continuous monitoring delivers proactive risk detection, sustained compliance, and operational efficiencies that help reduce churn and incident rates. Near-real-time alerts let teams restrict access, request re-assessments, or ask for additional documentation without waiting for periodic audits. That shortens the window of exposure and supports data-driven worker-status decisions while lowering manual re-screening. ROI shows up as faster incident resolution, fewer customer safety events, and more targeted use of verification resources based on current
risk.
How Do Real-Time Alerts Support Gig Workforce Safety and Compliance?
Real-time alerts highlight specific changes—new public records, license suspensions, credential expirations—and should be triaged by priority so teams respond proportionally. A practical workflow is: receive alert → automated contextual enrichment (attach worker ID, role, recent checks) → risk scoring and priority assignment → human review and temporary restriction if needed → communicate with worker and document outcome. Alerts typically include new criminal filings, driving-record updates, and credential-status changes; each requires distinct escalation rules and recordkeeping to meet compliance needs.
- Real-time detection: Identifies new records quickly so platforms can act.
- Reduced manual re-screening: Automates ongoing checks and lowers administrative load.
- Sustained trust: Shows commitment to safety and protects brand reputation.
Monitoring uncovers risks one-time checks miss and enables measured, auditable responses.
How Does Partnering with a Specialized Provider Like Vetty Enhance Background Check Reliability?
Working with a specialist consolidates verification, compliance, and onboarding into a single, integrated workflow that reduces handoffs and increases confidence in results. Specialist providers bring deep domain knowledge in applying FCRA, Ban-the-Box, and state rules consistently, and they typically offer accreditation and security controls that support audits.
Vetty provides an integrated platform with verification, compliance automation, and onboarding modules that map directly to the five-step screening framework—helping platforms scale reliable checks with transparent timelines. The section below summarizes module benefits and shows a brief example of operational impact.
What Are the Advantages of Vetty’s Integrated Platform: VettyVerify™, VettyComply™, and VettyOnboard™?
Vetty’s modular design aligns identity verification, compliance, and onboarding to cut handoffs and speed activation while preserving audit trails and state-aware logic. VettyVerify™ focuses on identity and document authentication to reduce mismatches and fraud; VettyComply™ enforces jurisdictional rules and automates adverse-action workflows; VettyOnboard™ manages candidate communication and activation dashboards. Together, these modules drive efficiency through consolidated dashboards and reports and provide compliance support with transparent timelines and a dedicated compliance team. Vetty’s PBSA accreditation and SOC 2 Type II certification add independent validation of our processes and controls.
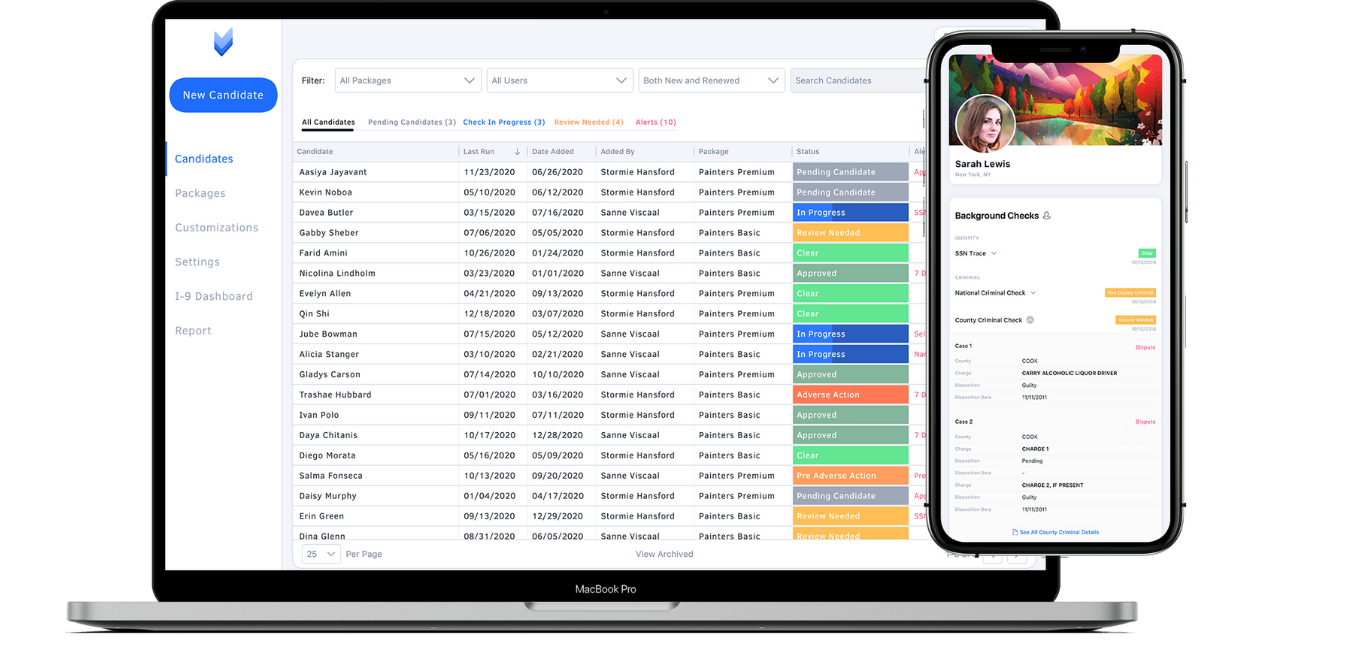
| Product/Feature | Capability | Benefit / Measurable Outcome |
|---|---|---|
| VettyVerify™ | Automated identity verification and document authentication | Fewer false matches, faster identity resolution, improved match confidence |
| VettyComply™ | State-aware compliance engine and adverse action automation | Consistent FCRA adherence, reduced legal risk, auditable decision logs |
| VettyOnboard™ | Onboarding workflows, candidate messaging, and activation dashboards | Shorter time-to-activation, higher completion rates, transparent timelines |
How Has Vetty Helped Gig Platforms Improve Safety and Onboarding Efficiency?
Specialist platforms help gig marketplaces reduce onboarding ambiguity and speed activation by combining verification, compliance automation, and candidate communications into one workflow. In one partnership example, a platform needed clearer timelines, consolidated worker profiles, and scalable compliance handling; an integrated approach delivered more consistent verification outcomes and clearer status reporting for internal teams and workers. Typical gains include reduced time-to-hire, fewer manual escalations, and more defensible adverse-action decisions thanks to audit logs and standardized templates. When evaluating providers, prioritize their ability to deliver verified profiles, clear timelines, and built-in compliance controls when calculating vendor ROI.
We invite you to book a demo of the Vetty platform.
What Are the Best Practices for Streamlining Background Checks and Onboarding in the Gig Economy?
Streamlining background checks for gig workers means balancing prioritized, risk-based screening with parallel processing, clear candidate communication, and measurable KPIs that track speed and safety. Best practices include building role-based templates, automating consent capture and parallel ordering of checks, and using a tiered verification approach so only high-risk roles undergo heavier screening. Candidate experience improvements—clear timelines, progress updates, and short explanations of next steps—boost completion rates and reduce drop-offs. The sections below offer workflow optimizations HR teams can implement and a compliance checklist to keep screening
transparent and defensible.
How Can HR Teams Optimize Screening Workflows for Gig Workers?
Optimization depends on role-based templates that trigger the right checks automatically and on parallel processing that runs identity, criminal, and driving searches concurrently to shorten total time-to-activation. Use automation to capture consent, apply jurisdiction-specific rules, and surface exceptions for human review. Track KPIs like average time-to-clear, completion rate, and percent of cases needing manual escalation. Candidate-facing status pages and concise messages reduce confusion and abandonment, while batching and scheduled verification windows help manage provider throughput. Iterate on templates quarterly using incident data and onboarding metrics to refine
speed versus risk trade-offs.
What Compliance Steps Ensure Transparent and Trustworthy Background Checks?
Defensible screening requires clear disclosures, auditable consent records, a documented adverse-action process, and retention policies aligned with privacy obligations. Provide candidates with a plain-language disclosure explaining which checks will run and why, capture timestamped consent stored with the report, and follow an evidence-based adverse-action workflow that includes pre-adverse notices and access to the report. Keep auditable logs of decision rationale and communications, protect sensitive records, and regularly review policies against changing state rules. Train staff on fair-chance hiring principles to preserve trust and legal compliance.
- Role-based screening templates: Automate check selection by role to ensure consistency.
- Parallel processing: Order multiple checks simultaneously to reduce activation time.
- Transparent candidate communication: Provide clear timelines and status updates to reduce drop-offs.
- Documented compliance workflows: Maintain disclosures, consent records, and adverse-action logs for auditability.
These practices create a smoother candidate experience while preserving the legal and operational safeguards required to scale a safe, compliant gig workforce.
Frequently Asked Questions
What are the common challenges faced during background checks for gig workers?
Common challenges include inconsistent regulations across jurisdictions, the need for rapid processing because of high turnover, and the complexity of assessing role-specific risk. Platforms must balance thorough screening with a friction-free candidate experience to avoid deterring applicants. The variable nature of gig work can also mean incomplete or inconsistent data, which complicates reliable, compliant screening.
How can organizations ensure candidate privacy during background checks?
Protect candidate privacy by following strict data-protection policies and applicable laws such as GDPR. Obtain explicit consent before running checks, store personal data securely, and limit access to authorized staff. Clearly explain how data will be used and retained, and verify that third-party vendors meet the same privacy and security standards.
What role does candidate communication play in the background check process?
Clear candidate communication reduces uncertainty and improves completion rates. Tell candidates what checks will run, expected timelines, and next steps. Provide status updates, explain delays when they occur, and offer a way to ask questions or dispute findings—these practices build trust and lower abandonment.
How can technology streamline the background check process for gig workers?
Technology automates routine tasks—consent capture, data entry, and record retrieval—and speeds verification with AI-driven record linkage and digital identity checks. These tools reduce turnaround times, improve accuracy, and let teams focus human review on higher-risk cases. Integrating automation into the workflow improves compliance and operational efficiency.
What are the implications of non-compliance in gig worker background checks?
Non-compliance can result in fines, litigation, and reputational harm. Violating laws like the FCRA or local Ban-the-Box statutes can lead to penalties and lost trust from candidates and customers. Non-compliance also increases the risk of hiring unsafe or unqualified workers, which can produce costly incidents and damage your brand.
How can continuous monitoring benefit gig worker safety and compliance?
Continuous monitoring offers ongoing oversight after onboarding, enabling teams to detect new incidents—criminal activity, license suspensions, credential expirations—quickly. Near-real-time alerts let you take proportionate action, reducing exposure and supporting evidence-based decisions about worker status. Ongoing vigilance protects customers, platforms, and workers alike.
Conclusion
A structured, role-based approach to background checks improves safety, compliance, and operational efficiency for gig workforces. Using modern verification technology, clear templates, and continuous monitoring lets platforms reduce risk while keeping the candidate experience smooth. Partnering with a specialist provider like Vetty further strengthens trust with audit-ready processes and state-aware controls. Learn how our solutions can streamline your screening and onboarding—book a demo to see it in practice.
Let’s Build Your Hiring Advantage
Want to screen faster, place sooner, and win more? Let’s talk.






